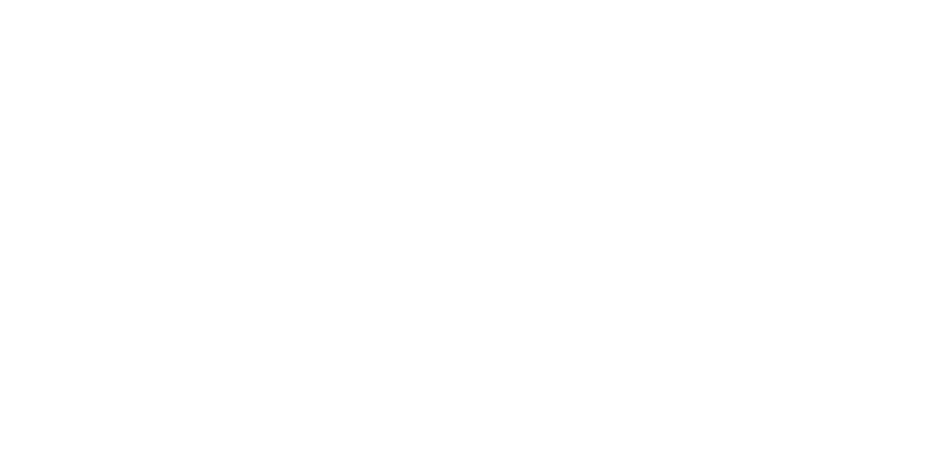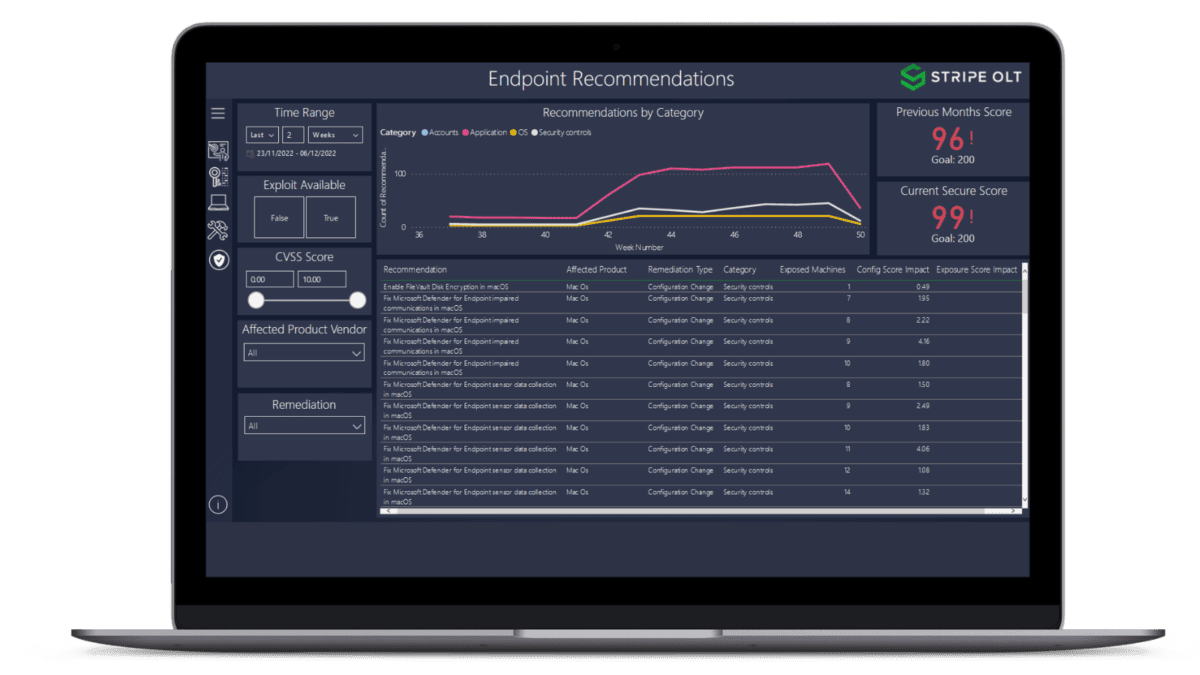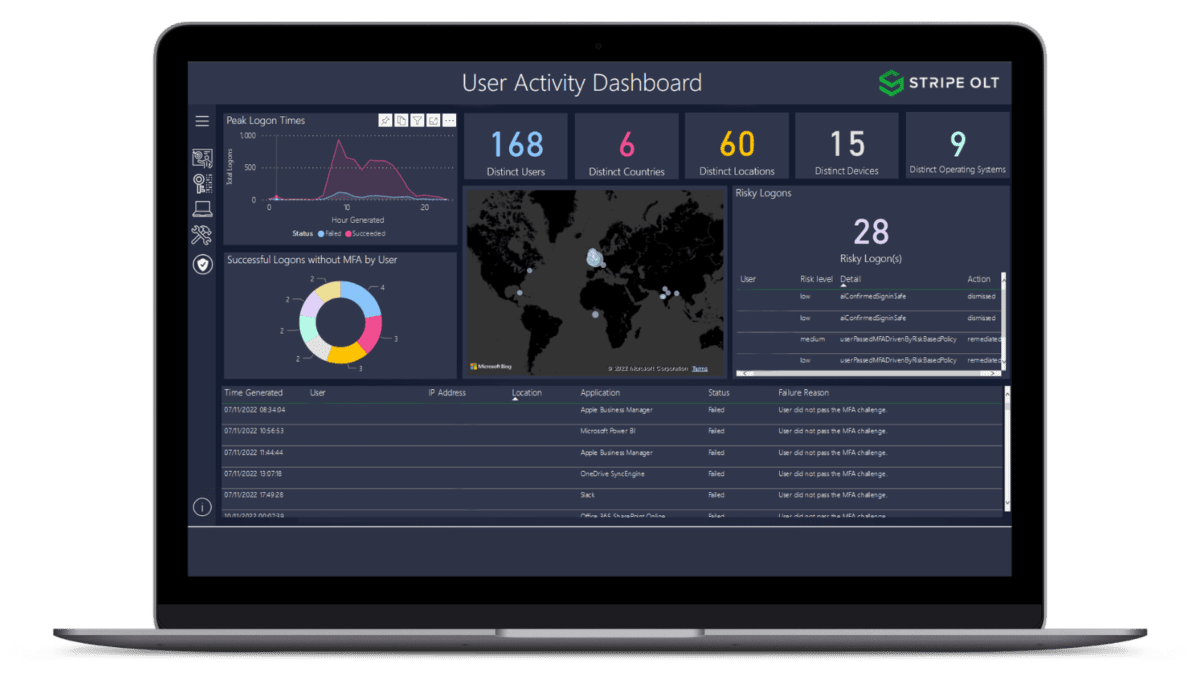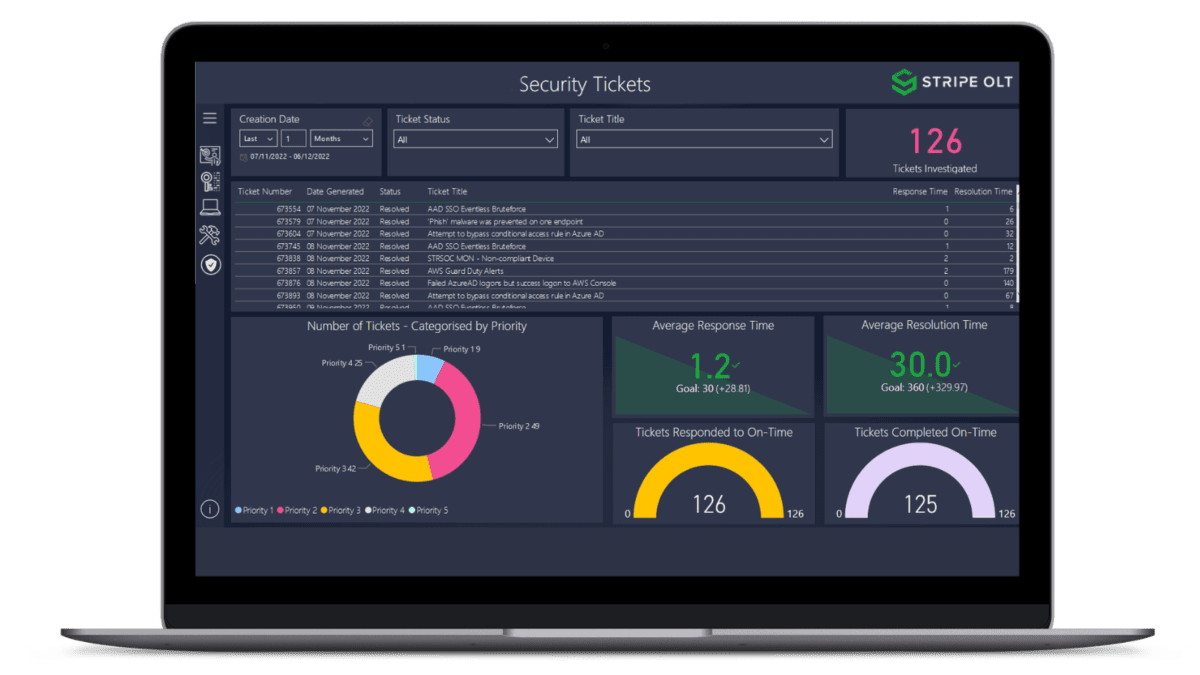
"Moving to E5 has been really good from a security point of view... Now we can get a holistic view of what’s going on, which helps us to make changes and recommendations for future plans."






Kickstart Your FastTrack Journey
Fill out the short form below to express your interest in our FastTrack programme, and we’ll be in touch soon.