
“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call-back.
First we need a few details.

“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call
First we need a few details.


The cloud evolution has helped to shape the current digital landscape, but with fast progress comes an ever-changing threat landscape, and in turn a shifting set of security challenges.
Our security Vulnerability Assessments help with this challenge by defining, identifying, classifying and prioritising vulnerabilities in computer systems, applications and network infrastructures.
















IASME Cyber Assurance

Microsoft Solutions Partner

GIAC Security Essentials

ISO 27001

Cyber Essentials
Plus

CREST Certified






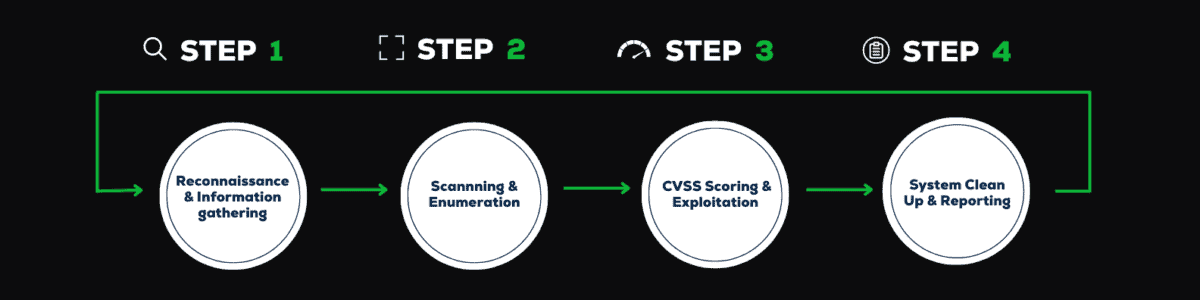
A vulnerability assessment is a testing process designed to identify and evaluate security defects within a specified timeframe. It encompasses a range of techniques, both automated and manual, to detect vulnerabilities with different levels of thoroughness and a focus on achieving comprehensive coverage. The goal is to identify and prioritize security issues based on their severity. Vulnerability assessments play a critical role in proactively identifying and addressing security weaknesses in your organization. By regularly assessing vulnerabilities, prioritizing remediation efforts, and strengthening your security controls, you can enhance your business’s resilience against cyber threats and reduce the likelihood of successful attacks.
A vulnerability assessment identifies and analyzes vulnerabilities in a system through automated scanning and manual verification. The findings are prioritized based on severity, and a detailed report is generated, including recommended mitigation actions. Remediation steps are taken to address the vulnerabilities, ensuring a stronger security posture and mitigate potential risks.
The costs associated with a vulnerability assessment include service provider fees, scanning tools/software, system complexity, number of endpoints analyzed and any additional services required, such as remedial works. Pricing can vary based on these factors and the specific needs of the organisation.
For many organisations it’s almost impossible to check your own homework, so outsourcing a vulnerability assessment brings benefits such as access to expertise and experience, objectivity, time efficiency, specialized tools, cost-effectiveness, scalability, and compliance support. It allows organisations to leverage cybersecurity professionals, streamline processes, and focus resources on remediation efforts effectively.