“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call-back.
First we need a few details.
Keep up to date with the experts
Get insights direct to your email inbox
Follow us on social

“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call
First we need a few details.

As you may have heard, there have been a number of high-profile Cyber Attacks covered in the media recently – Santander, Ticketmaster, and a selection of NHS trusts in London have all experienced large scale, targeted cyber attacks.
Naturally, we’ve had a fair amount of people asking for advice and as such, I wanted to collate some information for those that want to understand more, and potentially help a few of those that want to know what they should be doing to avoid falling victim.
First, let’s explore the attacks that have taken place on the NHS.

THE BACKGROUND
Two NHS trusts have had to cancel non-emergency operations after a ransomware gang targeted Synnovis, a third-party company that provides testing services for multiple hospitals.
Synnovis’ IT systems were completely locked out. It was theorised that Russian cyber-criminal gang ‘Qilin (Agenda)’ were behind the attack, though initial access and a root cause has yet to be disclosed – see Synnovis Statement / The Standard – NCSC Statement.
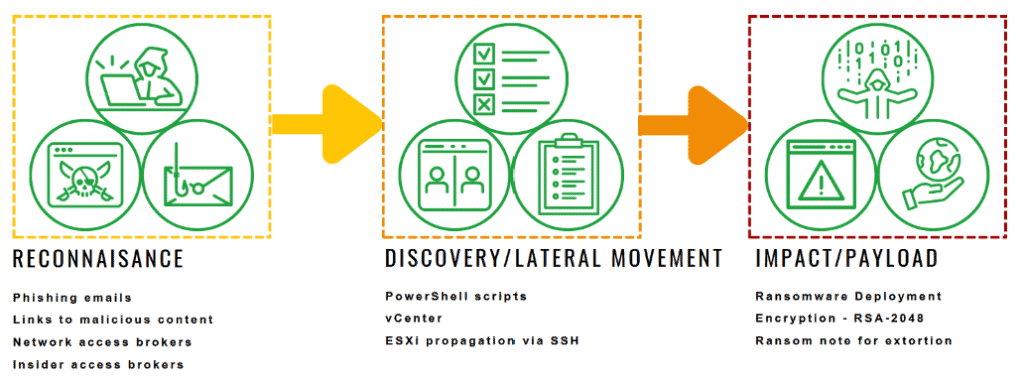
Qilin target a large variety of industries, Manufacturing, Construction, News and Entertainment, Healthcare and more.
Their focus is generally on phishing emails that contain malicious links, after gaining initial access the threat group will move laterally through an environment searching for sensitive data locations to mark for encryption.
During the encryption stage, the threat group places a ransomware note in each infected directory. This double extortion method causes mass disruption by locking data, providing more leverage when trying to extort victims for financial gain. See Source.
This particular strain of ransomware targets VMware Esxi servers, which are used by many corporations for virtual machine hosting. A full analysis can be found here.

A group known as ‘Shiny Hunters’ posted information on the dark web stating that they had collected data from 30 million individual bank accounts, which included account numbers, balances, credit card numbers and HR information for staff. See Source.
Again, ‘Shiny Hunters’ have claimed to have stolen data including names, addresses, phone numbers and partial credit card details from end users. There is estimated to be around 1.3TB of data stolen, and the threat group is reportedly attempting to sell this information for $500,000 on breach forums. See Source.
Both data breaches have been highlighted as having been from the same source, a cloud platform known as ‘Snowflake’ which is widely used for data storage, processing, and analytics.
Snowflake, and their cyber security providers CrowdStrike and
Mandiant released the following statement regarding the breach:
“We have not identified evidence suggesting this activity was caused by a vulnerability, misconfiguration, or breach of Snowflake’s platform.
We have not identified evidence suggesting this activity was caused by compromised credentials of current or former Snowflake personnel.
This appears to be a targeted campaign directed at users with single factor authentication.
As part of this campaign, threat actors have leveraged credentials previously purchased or obtained through info stealing malware.”
“Credentials leveraged in the attack were previously purchased or obtained through info stealing malware, adding that Snowflake did find evidence that a threat actor obtained personal credentials to and accessed demo accounts belonging to a former employee.“
See Source.
Whilst we won’t know the exact attack vector until official reports are made available, based on public information it’s likely that the data breach followed the following path:
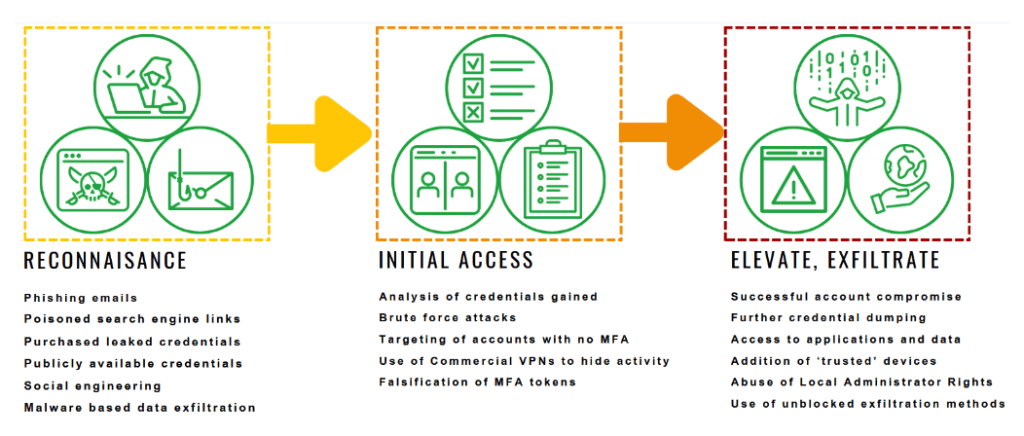
In light of the recent high-profile cyber attacks, it’s clear that robust cyber security measures are more critical than ever. At Stripe OLT, our Security Operations Center (SOC) operates 24/7 to ensure our clients are protected from these types of evolving threat.
Using advanced threat intelligence and proactive threat hunting techniques, we block harmful content and intercept phishing attempts to safeguard our clients’ data. And crucially, our team continuously monitor identity assets to detect and respond to potential breaches as and when they happen.
If this sounds like something you’d benefit from, get in touch with our team today.