“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call-back.
First we need a few details.
Keep up to date with the experts
Get insights direct to your email inbox
Follow us on social

“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call
First we need a few details.

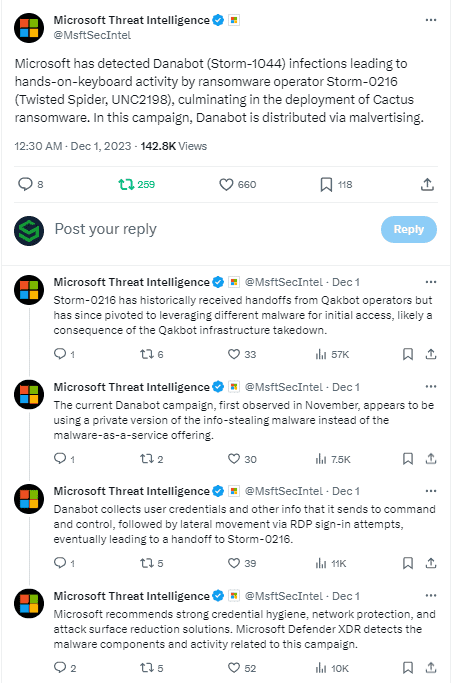
This month, Microsoft released a series of posts on X, warning about a new wave of CACTUS ransomware attacks that leverages malvertising.
Identified earlier this year, the tactics we are seeing from this group revolve around a spreading ‘Danabot infections’ via malvertsing, which are known to be extremely difficult to both identify and avoid.
According to Microsoft, these Danabot infections enabled:
“hands-on-keyboard activity by ransomware operator Storm-0216 (Twisted Spider, UNC2198), culminating in the deployment of CACTUS ransomware,”.
Microsoft Threat Intelligence
For those that are new here, Malvertising by definition, is a cyber threat that involves the distribution of malicious software or malware through online advertisements.
Through this technique, we see cybercriminals embed harmful code within seemingly harmless ads and exploiting vulnerabilities in web browsers or plugins to infect devices.
The impact of malvertising on its victims is extensive. The goal of malvertisers is to steal as much sensitive information they can (identification, financial data and contact data) with the purpose of selling the valuable information for the highest price.
Twisted Spider have essentially carried out a series of impactful ransomware attacks utilising the CACTUS ransomware. CACTUS is a relatively new variant and has already become a fan-favourite amongst ransomware operators, mainly due to its effectiveness in data theft and system encryption. Twisted Spider is known to utilise a range of entry points to infiltrate a victim’s system, most commonly they have used phishing emails, malvertising and the exploitation of software vulnerabilities. Once inside a victim’s system, CACTUS encrypts the essential files and demands cryptocurrency ransoms for decryption keys. As you can see from the tweets from Microsoft Threat Intelligence, this DanaBot campaign was first identified in November of this year, Microsoft noticed that the threat actors employed a private version of the popular info-stealing malware instead of the malware-as-a-service offering.
DanaBot, a sophisticated banking Trojan written in Delphi, surfaced in 2018 with an initial focus on Australian and Polish users. Over time, its operations expanded to include Italy, Germany, Austria, and Ukraine. The danger of this Trojan lies in it’s modular structure which enables the addition of new functionalities through plug-ins, it evolves continuously and DanaBot has been part of campaigns targeting users in Australia, North America, and Europe. Recent attacks in November involved the transmission of stolen credentials to a server controlled by threat actors, followed by attempts at lateral movement through RDP sign-ins and ultimately deploying the CACTUS ransomware.
In addition to the ongoing campaign by the Twisted Spider group, there are emerging reports of CACTUS ransomware exploiting critical vulnerabilities in the widely-used data analytics platform, Qlik Sense. Despite its effectiveness in data analysis and visualisation, Qlik Sense, like any software, may have vulnerabilities susceptible to exploitation. Malicious actors can leverage these vulnerabilities to gain unauthorised access to sensitive data, disrupt business operations and demand substantial ransoms for encrypted file release.

Although Twisted Spider were using the Danabot Trojan as noted above, there are a variety of payloads we commonly see in a malvertisings attack…
Malware: Short for malicious software, malware refers to any software intentionally designed to cause harm to a computer system, network, or user. It aims to disrupt, damage, or gain unauthorised access to computer systems, steal sensitive information, or extort users.
Spyware: Spyware is a type of malware designed to covertly gather information from a computer or device without the user’s knowledge or consent. It typically monitors and collects data on user activities, such as keystrokes, web browsing habits, and personal information . It then transmits this personal information to a malicious third party.
Ransomware: Ransomware is a type of malware that encrypts files on a computer or network, rendering them inaccessible. Hackers demand a ransom, usually in cryptocurrency, for the decryption key.
Malicious cryptomining: Malicious cryptomining, also known as cryptojacking, refers to the unauthorised use of a computer’s processing power to mine cryptocurrencies. In this form of cyberattack, attackers inject malicious code into a victim’s system, often through compromised websites or malware, to secretly harness the computational resources for cryptocurrency mining. The victim’s device suffers performance degradation, increased energy consumption, and potential hardware damage. The mined cryptocurrency is then typically sent to the attacker’s wallet.
Adware: Adware is a type of software that displays unwanted advertisements on a computer or device. Typically, adware is bundled with other software, and once installed, it generates intrusive advertisements, such as pop-up ads or banners, disrupting your user experience.
As you have mostly likely gathered by now, malvertising can be tough to detect and can cause quite the headache once it’s activated.
But how does it cause so much damage?
Malvertising attacks often employ exploit kits, specialised malware that scans and exploits system vulnerabilities. Once installed, the delivered malware operates like any other, causing file damage, redirecting internet traffic, monitoring user activity, stealing data or creating backdoor access points. While less common, malvertising attacks can occur without user interaction, utilising methods such as “drive-by downloads” exploiting browser vulnerabilities, forced browser redirects or executing scripts like Javascript or Flash to display unwanted or malicious content.
It’s all well and good knowing how malvertising works, but it is critical to understand what you can do as an individual user or as an organisation, to defend against malvertsing.
To make things easier, here are my top tips for dodging malvertsing scams:
Keep your Software Updated: It is vital to regularly update web browsers, plugins, and operating systems, in order to patch vulnerabilities which malvertisers can exploit.
Use Security Software, like Microsoft Defender: Employ robust antivirus and anti-malware software to detect and mitigate malvertising attempts.
Exercise Caution: Be vigilant while clicking on ads, especially those prompting software downloads or suspicious actions.
Empowering yourself with knowledge about the characteristics of malvertising is your strongest shield in when it comes to defending against this attack vector. Malvertising manifests in various ways, and as we approach the holiday season, here are the most prevalent forms to be vigilant about…

Many malvertising attacks necessitate user interaction with the infected ad, making it difficult to determine which website visitors may be affected. Although preventing malvertisement infections is no simple feat, users can mitigate risks by taking these steps this festive season:
Employing a reputable antivirus program is a crucial initial step in strengthening your cyber security. I recommend Microsoft Defender Antivirus, for it’s real-time and always on protection from threats like malvertising. Equally important is consistently updating your anti-virus, particularly for effective malvertising prevention.
Stay vigilant for false security apps that claim to protect you but may compromise your privacy. Stick to trusted providers such as Microsoft Authenticator, for your authentication needs to ensure reliability.
While ad blockers alone may not offer comprehensive protection, they serve as a valuable starting point. These tools effectively block pop-ups and banner ads, reducing the risk of encountering malicious content. However, it’s essential to note that fraudsters have devised workarounds against ad blockers, necessitating their use alongside other tools like antivirus programs.
Maintaining an up-to-date browser is essential to mitigate vulnerabilities, particularly against drive-by download attacks. Regarding browser plugins, uninstalling Flash and Java is recommended. Java is no longer supported, and Flash is slated to end its life in 2020. To prevent potential security risks, uninstall these plugins promptly.
It is imperative to stay up to date on developing incidents and behaviours of threat actor groups like Twisted Spider. I personally recommend follow Microsoft Threat Intelligence on Twitter to read real-time, trusted updates from the experts.
In summary, Twisted Spider poses a serious cyber security threat to both organisations and individuals, but malvertising is far from a new technique.
Groups like Twisted Spider have a plethora of attack types they can employ, such as pop-ads, drive-by downloads and malicious web widgets, making them a difficult group to identify. However, taking simple precautions such as updating your antivirus software, using a blockers and staying in the know, can strengthen your security posture and aid you in the fight against malvertising. I’d also highly recommend you follow Microsoft Threat Intelligence on X.
For those searching for support and guidance to proactively defend against threat groups like Twisted Spider, don’t hesitate to get in touch.
From Cyber Security User Awareness Training to our 24/7 Managed Cyber Security Operations Centre, we’re here to support and secure, wherever you need it most.