“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call-back.
First we need a few details.
Keep up to date with the experts
Get insights direct to your email inbox
Follow us on social

“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call
First we need a few details.

Over the past year, the cybercrime landscape has undergone a significant transformation in activities and tactics, surpassing anything we have previously witnessed. Traditional types of cybercrime and cyber criminals driven by financial motives, who typically gain initial access through email or phishing emails have abandoned the use of static and predictable attack chains.
Instead, they have adopted dynamic and rapidly evolving techniques.
This profound shift in types of cyber crime can largely be attributed to Microsoft’s decision to block macros by default, thereby compelling all participants in the threat actor hierarchy, from minor cyber criminals to seasoned individuals, to alter their operational strategies. In October 2021 and February 2022, Microsoft announced the default blocking of XL4 and VBA macros, respectively, for Office users. The implementation of these changes commenced in 2022.
Drawing from Proofpoint’s telemetry, which involves analysing billions of messages every day, researchers have detected extensive experimentation among threat actors in terms of malware payload delivery. This experimentation involves the utilization of outdated file types, unexpected attack chains, and a diverse array of techniques resulting in malware infections.
We can observe that various cyber criminal threat actors are engaged in experimentation, employing multiple attack chains and tactics for delivering malware. Researchers have identified that when a new threat behaviour or technique is adopted by one cyber criminal, multiple other cyberciminals follow in subsequent campaigns. Prior to April 2022, only a few initial access brokers (IAB) utilized LNK files in their threat campaigns. However, after four threat actors incorporated LNK files into their attack chains to deliver malware, including TA542 employing them for Emotet delivery, other threat actors began to adopt the use of shortcuts in their campaigns. Nonetheless, the popularity of LNK files diminished earlier this year, giving way to the prominence of other file types within attack chains. Cyber criminals tend to imitate one another for several reasons, there is an anticipation that new attack chains may yield better results compared to known behaviours and replicating existing attack chains is easier than creating new ones (reducing the testing and development efforts required by the cybercriminal).
OneNote Phishing
Research shows that OneNote documents for malware delivery started in December 2022, initially used by unattributed campaigns, this technique gained popularity among various cyber criminals, including initial access brokers (IABs). OneNote files contained embedded files hidden behind button graphics, and when users interacted with them, malware could be executed. However, the effectiveness of this method decreased over time as security measures and detection tools were developed.
Our senior Cyber Security Analyst, Joe. F, explored Supply Chain Phishing Attacks in his recent expert intel, mapping out the attack chain, detections and advice based on the behaviour he and fellow analysts observed in real-time incidents.
Microsoft’s implementation of Mark of the Web (MOTW) attributes to OneNote files in January 2023, along with the announcement of blocking embedded files with dangerous extensions in March 2023, contributed to the decrease in OneNote usage. These security measures aimed to improve detection and mitigate the effectiveness of OneNote as a malware delivery method.
The cyber criminal ecosystem has witnessed significant changes in attack chains, particularly among initial access brokers (IABs). These brokers play a crucial role in the cybercrime landscape by supplying access to affiliates and other threat actors, often selling it for profit. Typically, IABs obtain initial access through first-stage malware payloads like Qbot, IcedID, or Bumblebee, they then collaborate with ransomware operators to carry out data theft and encryption operations. IABs are opportunistic actors who may advertise access for sale on forums, acting as intermediaries between infiltrators and ransomware actors.
Case Study: IcedID
Researchers have monitored the activities of seven threat actors utilizing IcedID in approximately 250 campaigns since 2021, along with an additional 150 campaigns that remain unattributed. IcedID has been associated with subsequent ransomware infections like Quantum, RansomExx, and Conti. Before 2022, cyber criminals relied primarily on macros as the delivery method for IcedID malware, occasionally utilizing URLs leading to zipped JavaScript payloads. However, starting in early 2022, threat actors distributing IcedID, led by TA578 and unattributed threat clusters, began experimenting with new techniques for delivering the malware payload.
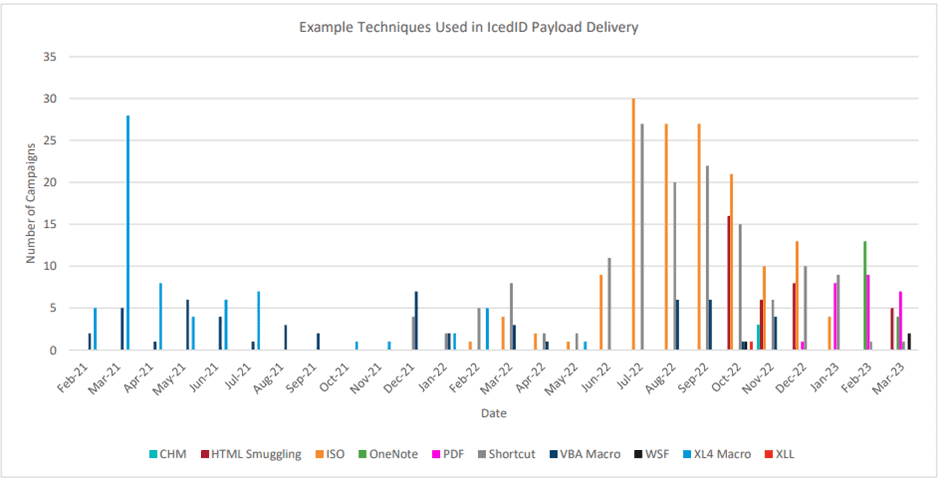
While we can identify consistent patterns among initial access brokers, targeted cybercrime threats exhibit diverse behaviour. The variation in tactics, techniques, and procedures (TTPs) used by targeted cyber criminal threats is likely attributed to their reliance on macros as the primary method of malware delivery before it became less effective. While some targeted threats heavily relied on macros as their main initial access vector, others completely disregarded macros in favour of alternative techniques that are gaining popularity in the broader threat landscape.
Case Study: TA2541
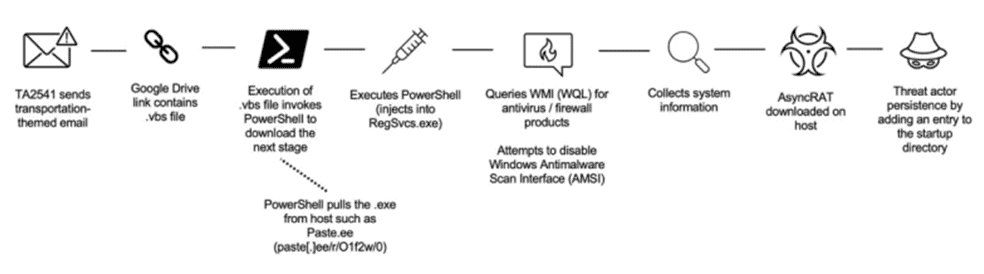
TA2541 is a cyber criminal actor known for focusing on aviation, transportation, and travel-related themes in their targeting. Analysts have been monitoring this actor since 2017, when initially they used Microsoft Word attachments containing macros to download remote access trojan (RAT) payloads. However, they swiftly shifted their tactics to delivering malware through URLs, often utilizing cloud services like Google Drive and Discord. This method led to the distribution of different scripts and compressed executables. In recent years, TA2541 has maintained consistency in their attack chains by relying on URLs for script-based delivery and avoiding the use of Office macros.
The landscape of cybercrime has significantly shifted since 2022, marked by the continuous experimentation and adaptation of techniques by tracked threat actors, particularly initial access brokers (IABs). This dynamic environment represents a new normal in the realm of cybercrime, where experienced cyber criminals are no longer relying on a limited set of techniques, but actively develop and refine new tactics. The agility demonstrated by these cyber criminals indicates their expertise, resources, and deep understanding of the evolving threat landscape.
These changes also have a direct impact on us defenders, the rapid adoption of new techniques requires swift response and adaptation from threat hunters, detection engineers, and malware analysts. We must quickly identify emerging trends in threat actor behaviour and develop effective defences to counter exploitation.
I predict that cyber criminals will continue to explore novel methods of payload delivery, while some cybercriminals may stick to certain techniques for extended periods, it is unlikely that a single attack chain or a set of techniques will remain consistently effective or possess the same longevity as the once-prevalent macro-enabled attachments.
Adaptability and continuous innovation will be key for both cyber criminals and defenders in this ever-evolving landscape.
Want to know more about how we can help protect your organisation against ever-evolving threats? Get in touch today.