“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call-back.
First we need a few details.
Keep up to date with the experts
Get insights directly to your email inbox
Follow us on social

“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call
First we need a few details.

Are you a recruiter or hiring for a vacancy within your business?
Do you receive CV’s on a regular basis from potential candidates for the job roles you are promoting?
If you answered ‘yes’ to either of those, then you may want to pay attention to this article.
In this Article I will cover:

Firstly, what, or who, is DEV-0538? This is the name given by Microsoft Threat Intelligence to a threat group they are tracking who tend to specialise in targeting recruitment staff.
Threat Intelligence on this group is very limited to the public right now and there is currently no direct mapping of DEV-0538 to any threat actors listed within Mitre Att&ck, but what we do know is:
“DEV-0538 is an emerging, financially motivated, cybercriminal group that has been observed targeting recruiters or other individuals via job application websites. They send phishing emails with an attachment containing hyperlinks, or the hyperlinks in the email body that lead to landing pages that serve their malware payloads to targets. Follow-on actions observed from DEV-0538 compromises include lateral movement, data exfiltration, and extortion of victims.”
–Microsoft
As a recruiter, some of the key details you will need to remain vigilant for are as follows (please note that mileage may vary here):
For the benefit of other security professionals, here I want to detail how these types of intereactions may manifest.
To begin with, the threat actors will create a fake LinkedIn account which they will use to send their “application” for job postings for a target organisation.
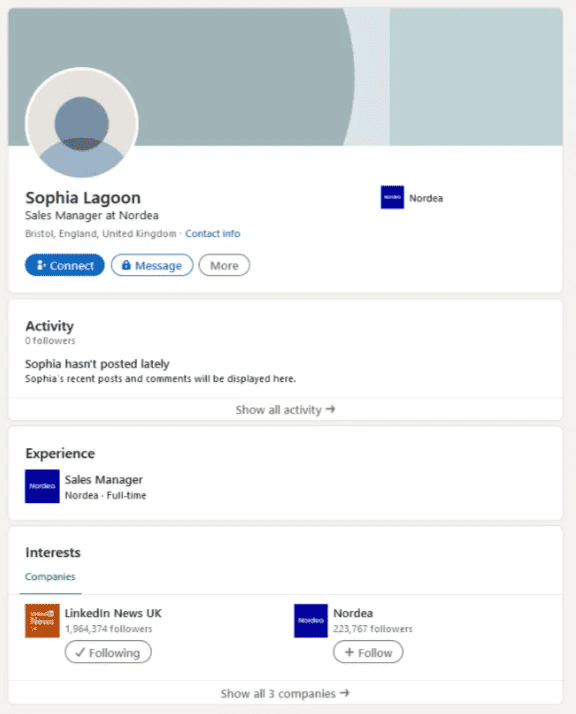
Fake LinkedIn page used by Threat Actor
Next, they will send a PDF document (format may vary) to the recruiter, or individual who is hiring. This document may be completely blank and will contain a hyperlink to their ‘personal website’ which will be named after the LinkedIn account they submitted the document from.
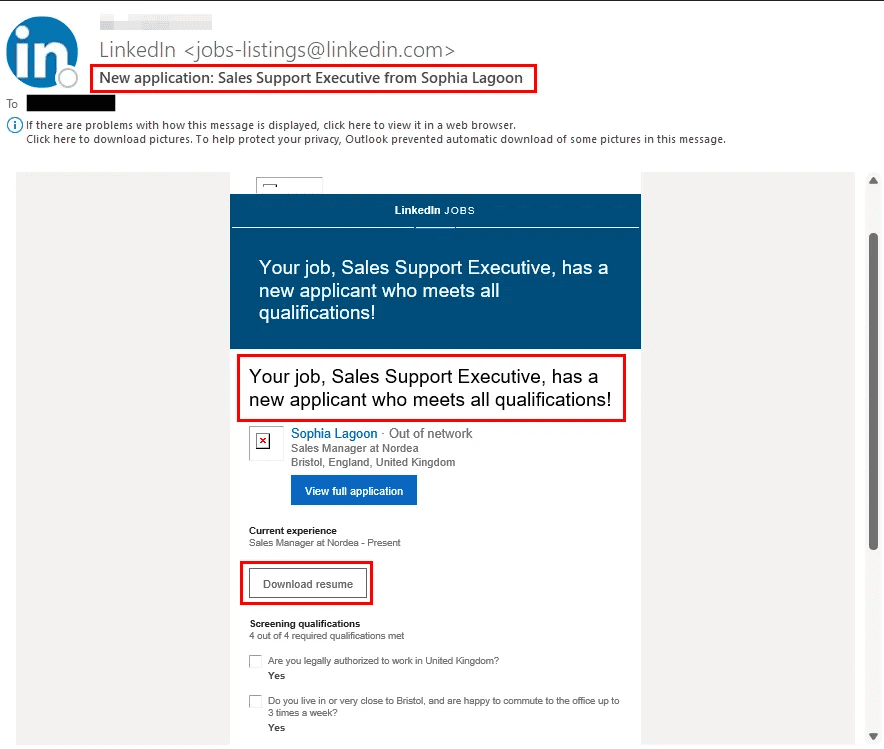
Email Received by Recruiter
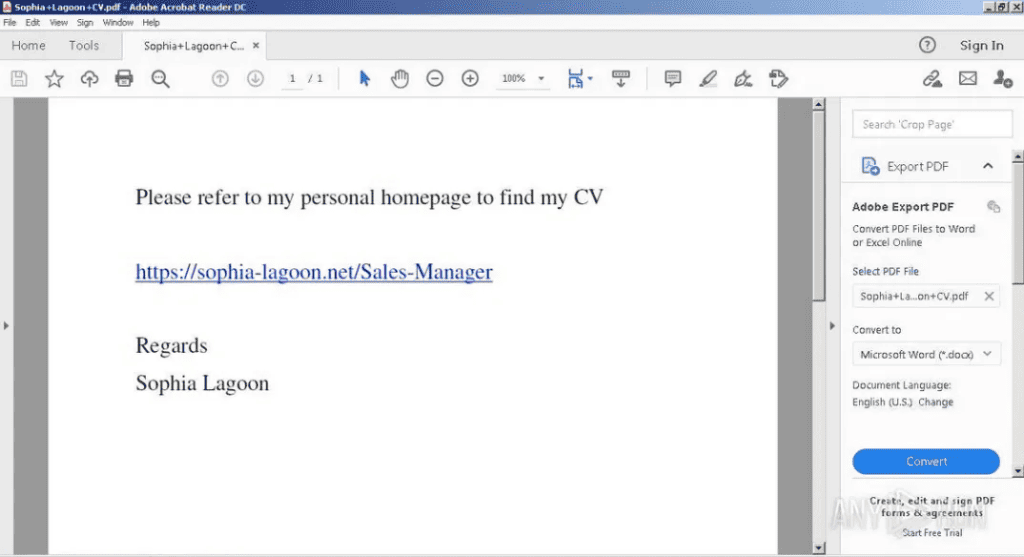
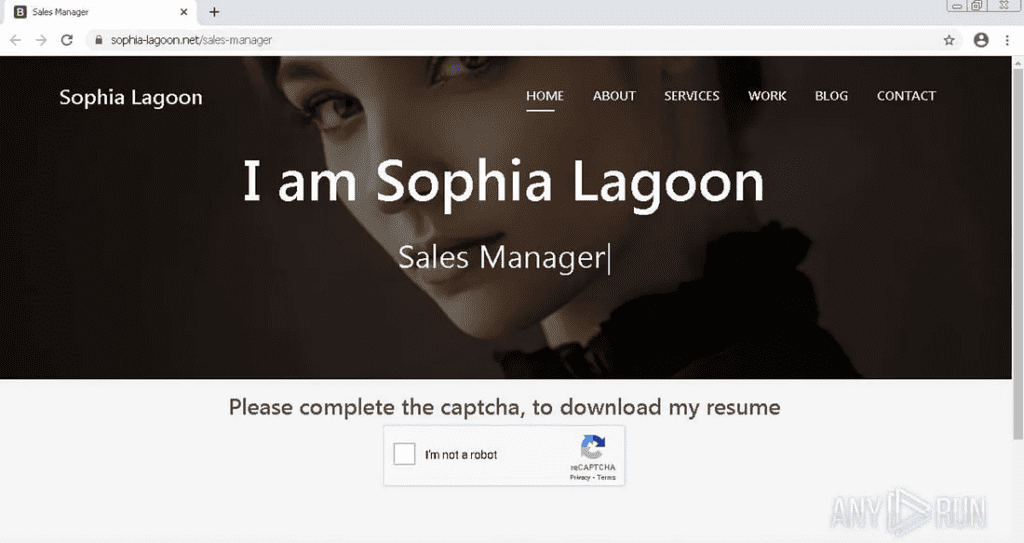
In this example, the actor created the online persona of Sophia Lagoon, with the website of https[://]sophia-lagoon[.]net. Depending on the sophistication, funding and resources the actor has, they will create very convincing websites which to the untrained eye will look completely legitimate. Following this, the victim is prompted to complete a CAPTCHA in order to download the candidate’s CV. This is their delivery method. Again as I’ve mentioned in other articles, this use of a CAPTCHA prevents security tools which may use static detection, from identifying and flagging the malicious download as this often requires human interaction to bypass. This is why end user training and remaining vigilant is so important regardless of your job title.
In some cases they may send malicious documents with embedded macros which will no doubt be detected and blocked, alternatively, policies blocking the use of macros in office documents will prevent the execution of any malicious code within the document.
After completing the CAPTCHA challenge, a countdown and download will commence. In this case, the file the victim would download is called “Sales Manager.zip”. This zip folder contains two files:
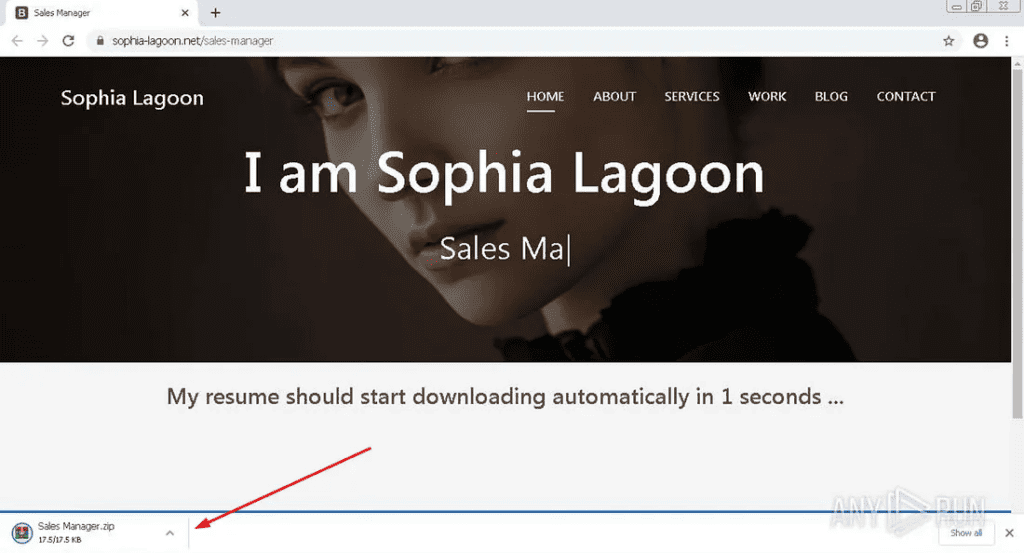
Sales Manager.zip being downloaded after completing Captcha Challenge
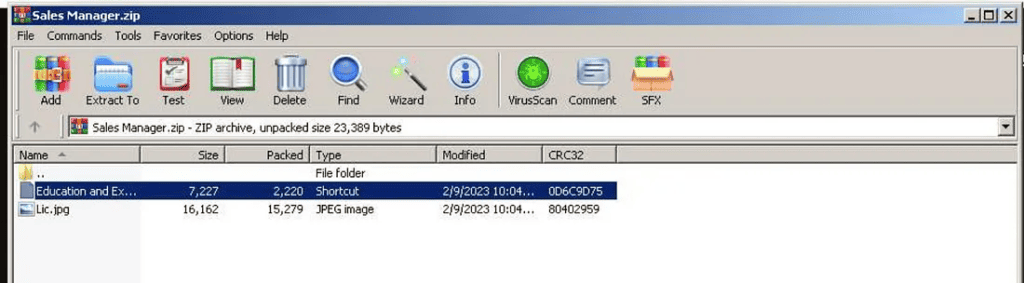
Education and Experience.lnk with Lic.jpg
Lic.jpg
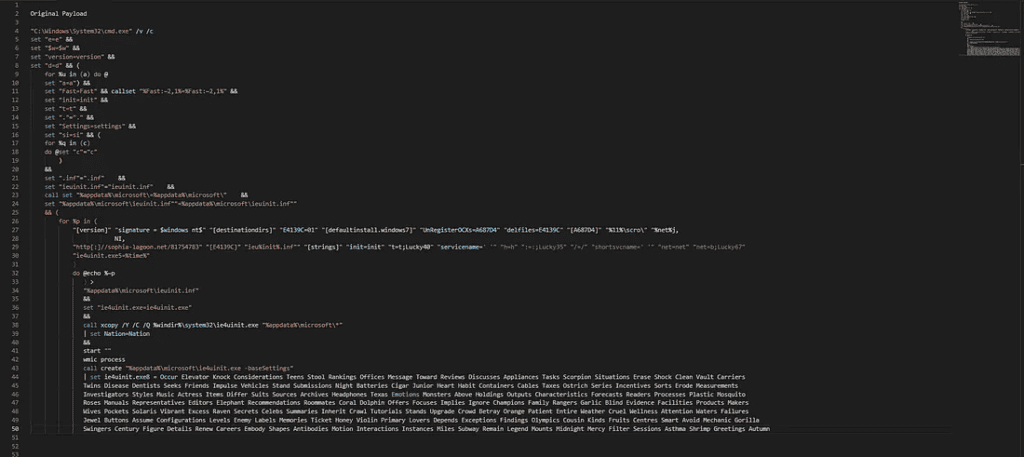
Payload executed by CMD on opening .lnk file
To summarise, DEV-0538 are a threat group known to Microsoft Threat Intelligence for targeting recruiters by posing as potential candidates for open job vacancies. The actors send malicious documents masqueraded as a candidate’s resume in order to phish their victim into downloading a malicious payload granting them initial access into a target network. From here, the malicious actors will continue to move laterally, establish persistence within a network and carry out their objectives where possible.
File: Sophia+Lagoon+CV.pdf
Hash: 9BE7E15234E9C9769076280B8FCAE753A649E44B3E0DF82AE2EDF275039E74E0
Virus Total:
https://www.virustotal.com/gui/file/9be7e15234e9c9769076280b8fcae753a649e44b3e0df82ae2edf275039e74e0/detection
File: ie4uinit.exe
Hash: c989cdcac84546c25258b480bee6d2f7ed27d41cb4538428be1649f522e4acdc
Virus Total: https://www.virustotal.com/gui/file/72daf26f6e15058a9fc47f3ba2bae13f5c3129b97c70ff484906a25e0ce7273b/relations
File: E4UINIT.EXE (different to above)
Hash: 72daf26f6e15058a9fc47f3ba2bae13f5c3129b97c70ff484906a25e0ce7273b
Virus Total: https://www.virustotal.com/gui/file/72daf26f6e15058a9fc47f3ba2bae13f5c3129b97c70ff484906a25e0ce7273b/relations
File: Education and Experience.lnk
Hash: 930506fba48983058ac1320684a8ab9d372d7d83265806fe995c6895964b3484
Virus Total: https://www.virustotal.com/gui/file/930506fba48983058ac1320684a8ab9d372d7d83265806fe995c6895964b3484/detection
IP Address: 142.11.222.59
Shodan: https://www.shodan.io/host/142.11.222.59
Domain: sophia-lagoon[.]net
URL: hxxps[://]sophia-lagoon[.]net/Sales-Manager
Below are a number of reports from sandbox solutions Joe Sandbox and AnyRun for anyone interested in looking into this further on their own. If you have any questions, please feel free to reach out!
Automated Malware Analysis — Joe Sandbox Cloud Basic
Automated Malware Analysis Report for CV — David Rolls.lnk — Generated by Joe Sandbox
https://sophia-lagoon.net/sales-manager — Interactive analysis — ANY.RUN
ie4uinit.exe (MD5: ACA03178C248B32343B03F4B9ACCE1B9) — Interactive analysis — ANY.RUN
https://app.any.run/tasks/6732da67-85cb-42bb-a279-9b195ee0e76a/
Want to stay at the forefront of cyber security? Make sure to sign up to our Newsletter Access Granted and gain monthly updates directly from our team.