
“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call-back.
First we need a few details.
Keep up to date with the experts
Get insights directly to your email inbox
Follow us on social

“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call
First we need a few details.
IBM have just released their coveted X-Force Threat Intelligence Index 2023 report, tracking new, existing and evolving threat insights, discovered over the last year.
This in-depth, 58-page report explores threat actor’s exploitation of the after-effects of a global pandemic, and the turmoil caused by conflict between Russia and Ukraine, as IBM states “creating exactly the kind of chaos in which cybercriminals thrive. And thrive they did.”.
Key findings include the usual suspects, such as phishing and ransomware, but interestingly IBM found that backdoor deployments became the most common cyber attack on organisations in 2023.
It’s no secret that data is becoming increasingly commoditised, and with stolen data on the dark web and selling for the highest price, hackers are benefitting more than ever.
This uptick in backdoor deployment (21% of incidents) even overtook levels of ransomware last year – however it’s worth noting that ransomware still claimed 17% of incidents, and about 67% of those backdoors were failed ransomware attempts, where defenders disrupted the backdoor before ransomware was deployed.
Extortion was the top impact from threat actors last year claiming 27% of incidents, IBM predicts this trend will continue to grow as hackers evolve and adapt to organisations defences. Europe saw the highest amount of extortion cases last year, making up 44% of all extortion cases. The UK was the most targeted country within Europe, accounting for 43% of cases.
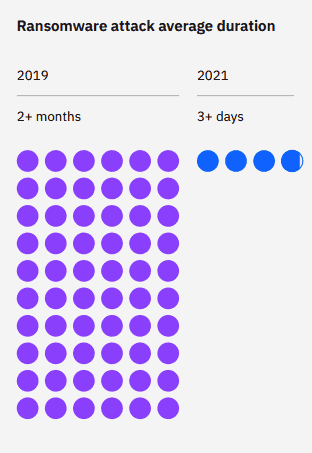
There was a slight decline in ransomware attacks last year, however IBM discovered that the time to execute attacks has reduced by 94%, meaning that what once took hackers months, now takes a couple of days. This new challenge highlights the importance of understanding how threat actors think and operate, as well as ensuring comprehensive defence systems are put in place.
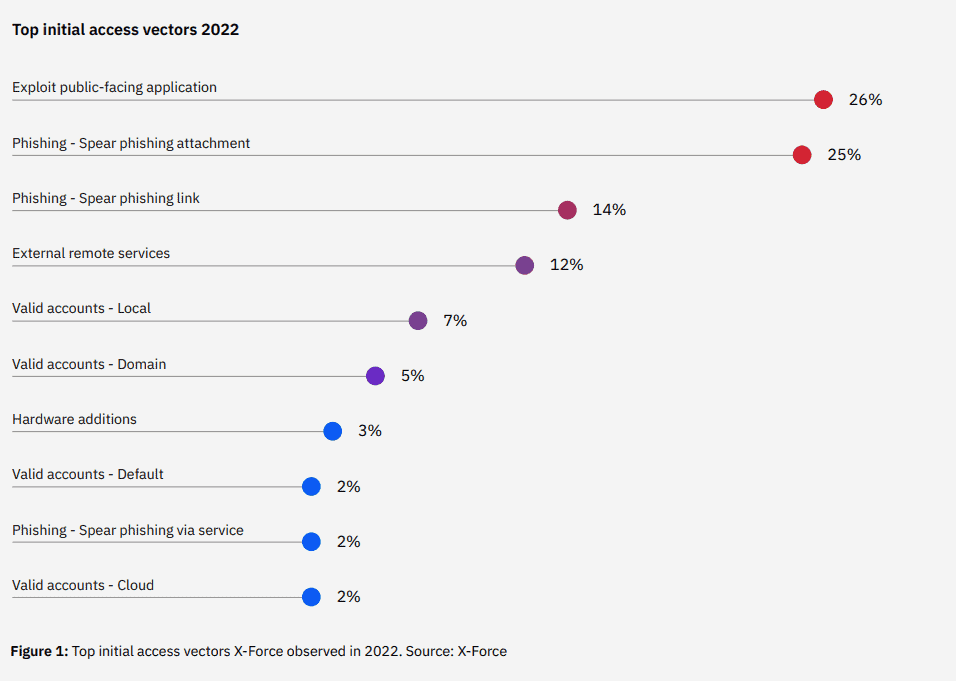
Phishing is still the favoured infection vector for cybercriminals attempting to exploit organisations, identified in 41% of attacks. 62% of all phishing attacks last year used spear phishing attachments, deployed by themselves or via service.
Since Microsoft announced its decision to block macros and improve security in Office, there has been a significant drop in infections by malicious macros, IBM states “Malicious use of ISO and LNK files escalated as the primary tactic to deliver malware through spam in 2022”.
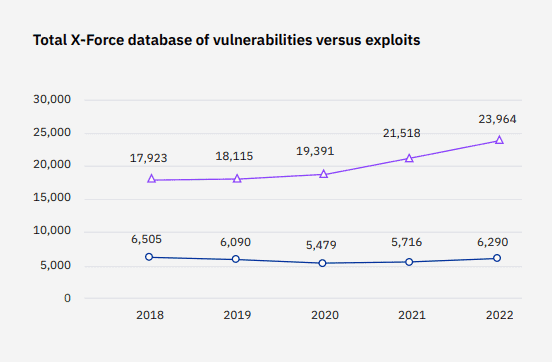
Regarding vulnerabilities, cybercriminals already possess a multitude of them, and they don’t need to spend resources searching for new ones as many old common. Unfortunately many common vulnerabilities still work just fine for them…
In 2022, X-Force reported an 800% rise in infections caused by exploiting the WannaCry vulnerability from 2017. This underscores the significance of organisations refining their vulnerability management plans and prioritizing critical patches.
Russia’s invasion of Ukraine sparked industry-wide and governmental predictions of high impact cyber operations in modern warfare — the severity of these predictions has not fully materialised.
However, what the IBM report does highlight is Russia’s deployment of a vast number of wipers against Ukraine targets, and that hacktivism has seen a resurgence from groups attacking both sides.
Modern warfare no longer means isolated geographical combat, and this war has reignited international hacktivist threats — spawning pro-Russian groups with global target lists — and has reshaped the cybercrime landscape in Eastern Europe.
Notably, defenders are adapting quickly to these wiper attacks and identifying, analysing and publicizing attacks to help prevent future victims. There were 8 identified wiper attacks last year, alongside the discovery and disruption of a planned Russian cyber attack on Ukraine’s electric grid in April 2022.
However, its not all doom and gloom it’s worth noting that defenders are proficiently utilizing the advancements in detection, response, and information sharing that have been established over the past few years. Several of the initial wiper attacks were promptly recognized, examined, and disseminated, aiding in shielding others from being targeted.
1. Manage your assets
The first step to securing your organisation against cyber threats is having a full understanding and overview of what data you have, what you are securing and what data is critical to your business. It is vital for organisations to include source code, credentials and any other data which is visible on the dark web, in their asset management program.
2. Know your adversary
Understanding how threat actors operate, recognising their level of expertise and identifying known tactics, techniques and procedures, will provide a holistic and thorough approach to securing your data. It is recommended to gain insight of the specific threat actors which are likely to target your industry, geography and your organisation.
3. Manage visibility
Once you have gained a comprehensive understanding of what data you are protecting and who could be trying to steal it, its important to have confident visibility of your enterprise. Meaning that cyber attacks can be detected and defended in a timely manner, to prevent disruptions on a much larger scale.
4. Challenge assumptions
Organisations should prioritise offensive testing and continuously assess their security through the eyes of a cybercriminal. To facilitate successful security systems, organisations must perform regular vulnerability assessments, penetration testing and red teaming to gain a full understanding of how a malicious actor could infiltrate and exploit their system.
5. Act on intelligence
Threat intelligence must be applied to every aspect of your organisation to stay one step ahead of adversaries. Applying threat intelligence to an understanding of who your attacker is and how they operate, enables you to effectively secure your data, develop high-fidelity detection opportunities and defend against cyber threats.
6. Be prepared.
‘Attacks are inevitable, failure doesn’t have to be’. IBM emphasizes the need for incident response plans, built specifically to each organisation’s environment. Maintaining security is essential and can be achieved through regular drills and modifications that aim to improve response, remediation, and recovery time.
Click here to read the full X-Force Threat Intelligence Index 2023