
“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”







“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call-back.
First we need a few details.
Keep up to date with the experts
Get insights direct to your email inbox
Follow us on social

“We needed to find solutions to a variety of issues whilst being a complex business, operating in a 24/7 environment. Stripe OLT listened and understood immediately the challenges we faced.”






Request a Call
First we need a few details.
In today’s hyper-connected digital landscape, cyber security has grown increasingly complex. Organisations are shifting operations to the cloud, enabling remote work, and engaging with third-party ecosystems, expanding the potential attack surfaces. Threat actors are exploiting this complexity with high-volume, multi-faceted attacks.
In a recent threat brief from Microsoft, titled ‘Anatomy of a modern attack surface’, the security powerhouse delves into the threats and trends which impact the 6 main attack surfaces in an organisation: email, identity, endpoint, IoT, cloud, and external.
So, we wanted to explore these areas further, to help you understand what your attack surface is, threats may present themselves in your organisation and what you can do to prevent malicious actors exploiting them.
Our resident expert and Head of Offensive Security, Tom Ellson, also shares his advice on each of these types of attack surface, to help you better understand the intricate reality of the modern attack surface.

What is the threat?
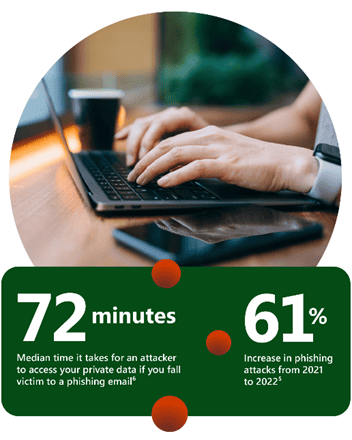
Email is a critical tool for organisations, but it’s a major threat vector. In 2022, 35% of ransomware incidents involved email, and phishing attacks surged by 61%.
Attackers increasingly use legitimate resources, making it hard to distinguish real from malicious emails. Detecting email-based threats is slow, and attackers can access data within 72 minutes, costing billions. Prevention of this vulnerability being exploited includes URL checks, disabling macros, and educating employees to spot malicious content. Expect attackers to improve social engineering in emails using AI. The Microsoft report shows that email threats will only evolve as organisations enhance defences.
What is the expert opinion?
These numbers are hard to ignore and emphasise why organisations must invest in strengthening their email defences. To address these challenges, consider adopting a multi-layered defence approach that combines email filtering solutions, threat intelligence feeds, and advanced detection tools. This multi-pronged strategy provides a strong shield against email-based threats. Moreover, implementing robust email authentication protocols like SPF, DKIM, and DMARC helps verify the legitimacy of incoming emails, reducing the risk of spoofing. Finally, I highly recommend embracing the zero trust model , which assumes no one should be trusted by default, whether inside or outside the organisation.
How can we help?:
User education is a dynamic and cost-effective approach to protecting your email and user accounts. Training empowers employees to become a critical part of the organisation’s defence, especially against email-based threats by recognising, reporting, and avoiding potentially harmful emails. When combined with technical safeguards and ongoing training, user education creates a robust cyber security strategy that can significantly reduce the risk of email-related security incidents.
Additionally, a well-equipped SOC is essential for combatting email cyber security risks. Stripe OLT’s proactive monitoring, rapid incident response, integration of threat intelligence, and collaboration with other IT providers collectively strengthens your organisation’s defences against email-related threats. Through continuous vigilance and coordinated efforts, opting for a SOC enhances an organisation’s resilience in the face of evolving email cyber security risks.
What is the threat?
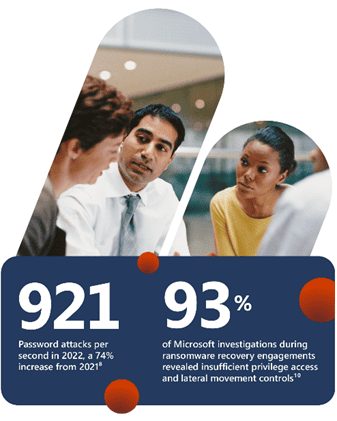
In today’s cloud-driven world, understanding and securing identity is critical. Password attacks soared to 921 per second in 2022, up 74% from the previous year. Threat actors are creatively evading multi-factor authentication, and advanced phishing kits are readily available for as little as $6 (£4.92) per day. Securing identity extends beyond user accounts to encompass cloud and workload identities, where compromised credentials can lead to data breaches. With identity attacks on the rise, maintaining a comprehensive understanding of identity and access remains critically important.
What is the expert opinion?
Identity security is critical consideration in cyber security and it’s an area where even the smallest vulnerability can have far-reaching consequences. The traditional network perimeter has faded, and identity has become the new frontier for protection. It’s not merely about user accounts; it’s about controlling access to critical assets and data. Privileged Access Management (PAM) is crucial – most breaches involve privileged accounts. PAM controls and monitors access to critical systems and data, Role-Based Access Control (RBAC) ensures users only access what’s necessary for their roles, reducing the attack surface. And lastly, password policies and multifactor authentication should be enforced, as strong password policies significantly reduce the risk of password-related breaches.
How can we help?
There are many way improve identity and access management, however a great way to quickly identity existing vulnerabilities is through a penetration test – these type of offensive security test are a vital tool in bolstering your organisation’s identity security. By simulating real-world attacks, they uncover vulnerabilities in your identity and access management systems, including weaknesses in user authentication, access controls, multi-factor authentication (MFA), and password policies. We also evaluate how well your systems detect insider threats and anomalies in user behaviour. This helps you mitigate the risk of both internal and external breaches. Furthermore, our tests validate the effectiveness of your Zero Trust architecture and assess your incident response readiness.
What is the threat?
Securing endpoints is increasingly challenging in today’s hybrid environment due to the proliferation of devices. Yet, it’s crucial for a strong security posture, as even one compromise can grant access to threat actors. BYOD policies have expanded unmanaged devices, significantly enlarging the endpoint attack surface. On average, an enterprise has about 3,500 unprotected connected devices. These unmanaged devices are enticing to threat actors due to limited security visibility, making users 71% more likely to be infected. Additionally, unmanaged devices on company networks open doors to broader infrastructure attacks, ensuring endpoint security is vital as threat actors continue targeting these devices.
What is the expert opinion?
Devices serve as common entry points for cyber threats and can provide access to sensitive data and critical systems, remote working has caused an influx of endpoints, ensuring their security is vital. Compromised endpoints can serve as launching pads for larger-scale breaches, especially with the prevalence of ransomware attacks. Additionally, the human factor in endpoints makes them susceptible to social engineering tactics like phishing.
Endpoint security is crucial for regulatory compliance and complements network security, forming a vital part of a holistic cyber security strategy. In an era of remote work, securing endpoints beyond the traditional perimeter is complex yet essential for comprehensive defence.
How can we help?
Numerous services and solutions can aid you in enhancing endpoint management and ensuring security, however as a Microsoft security solutions partner naturally we’d point you in the direction of implementing tools like Intune and Defender for Endpoint to reduce endpoint blind spots. The first step for many however is first establishing what endpoints you possess and in turn what to protect. Our cyber security experts provide a number of Microsoft security consultancy services that help you do just this – we’d recommend a call with our team to establish the depth of your requirements.

What is the threat?
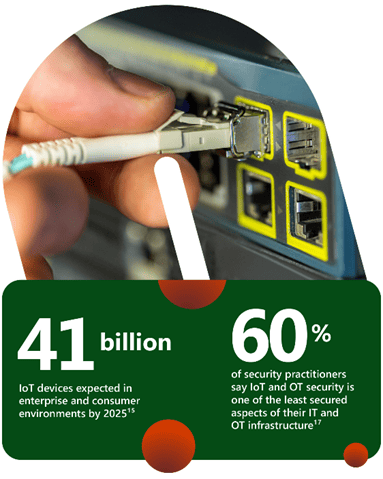
IoT (Internet of Things) is a frequently overlooked endpoint for cyberattacks, including devices like routers, cameras, and manufacturing equipment. As IoT device numbers surge, so do vulnerabilities, with a projected 41 billion devices by 2025. Threat actors are targeting IoT devices as traditional network defences improve. Once compromised, these devices serve as entry points for network monitoring, lateral movement, and broader attacks. Unfortunately, IoT security often lacks visibility, and many organisations lack proper safeguards, however, regulations are emerging to address IoT cyber security, reflecting growing concerns. Expanding cyber security regulations make it crucial for organisations to strengthen security and gain visibility across all attack surfaces.
What is the expert opinion?
As regulations tighten, organisations must prioritise IoT security to safeguard operations, data, and reputation . Cross-domain threats and reputational damage emphasise the importance of robust IoT security – while IoT devices have ushered in an era of unprecedented connectivity and convenience, their role as an attack vector cannot be underestimated. Organisations and individuals must remain vigilant, prioritise security in IoT deployments, and recognise the importance of securing this expanding attack surface.
How can we help?
Taking an offensive approach is highly recommended when it comes to IoT security and given the unique nature of IoT devices, specialised approaches are required. We’d recommend carrying out a variety of penetration tests to fully understand the scope and scale of your IoT attack surface.
We’d suggest:
IoT device pen testing: Many IoT devices interact with cloud services and back-end systems, so testing the security of these components is critical.
Network pen testing: Given that IoT devices are network-connected, evaluating the security of the network interfaces and communications is crucial.
Cloud pen testing: Many IoT devices interact with cloud services and back-end systems, so testing the security of these components is also critical.
Application pen testing: If the IoT device interacts with a user through an application, testing the security of this application is also vital.
What is the threat?
Organisations are rapidly migrating data and operations to the cloud, spanning SaaS, IaaS, and PaaS services across multiple platforms. However, many struggle to maintain comprehensive visibility and security, leading to extensive vulnerabilities. Shockingly, 84% of organisations hit by ransomware failed to integrate their multi-cloud assets with security tools.
The cloud’s broad adoption has introduced new attack vectors, particularly in cloud app development, where unknown vulnerabilities pose significant risks. A “Shift-left” security approach, integrating security from the start of app development, can mitigate these issues and prevent introducing these vulnerabilities in the first place.
Cloud storage represents a growing attack surface, with user data at risk due to misconfigured permissions. Cloud service providers can be vulnerable, evidenced by the Russia-linked threat group Midnight Blizzard (previously known as NOBELIUM) initiating phishing attacks against a cloud services provider to access privileged government customer accounts, in 2021. This incident is an illustration of contemporary cloud threats, the Microsoft report predicts an increase in cross-cloud attacks in the future.
What does the expert think?
While the cloud offers immense flexibility and scalability, it also presents unique security challenges. Organisations must approach cloud security holistically, understanding their shared responsibilities with cloud providers, and proactively address risks to protect their data and applications effectively. As the cloud continues to grow, it will remain a focal point for both cyber security advancements and threats. Misconfigurations, weak access controls, and poor identity management are common culprits in cloud security breaches. These issues can lead to data exposure, making data breaches one of the most significant risks in cloud security.
How can we help?
Our award-winning Security Operations Centre (SOC) safeguards cloud security by continuously monitoring cloud environments for threats and vulnerabilities. Using real-time monitoring and advanced technologies, our team of experts detect abnormal activities and promptly respond to potential threats. Our managed SOC also ensures compliance with industry regulations, analyse logs, manage security patches, and use behaviour analytics to identify insider threats. This proactive approach can help you safeguard your cloud assets and data from evolving cyber threats.

What is the threat?
Today, an organisation’s attack surface spans numerous cloud platforms, complex supply chains, and vast third-party networks. The internet is now integral to network security, demanding protection of online presence as much as internal assets. With the rise of Zero Trust, securing both internal and external surfaces is a massive challenge.
The global attack surface grows with the internet, evident in threats like phishing. In 2021, Microsoft’s Digital Crimes Unit removed 96,000 phishing URLs and 7,700 kits, closing 2,200 malicious email accounts.
The external attack surface includes suppliers, partners, unmanaged devices, and acquisitions, necessitating awareness to mitigate threats. In 2020, 53% of organisations suffered data breaches through third parties, costing $7.5 million on average to rectify. Understanding this expanded attack surface is crucial; otherwise, blind spots can lead to disruptive ransomware attacks, experienced by 61% of businesses in 2021.
What does the expert think?
To strengthen security, organisations should adopt an outsider’s perspective, gaining full visibility into their external attack surface. This reveals vulnerabilities across the organisation and its ecosystem, enhancing security and resilience against cyber threats. The internet is a multifaceted attack vector in modern cyber security, its global reach empowers cybercriminals to strike from anywhere, making attribution complex. Supply chain vulnerabilities amplify risks, while web application weaknesses offer exploitable entry points. Social engineering famously thrives on the internet, which only further emphasises the need for cyber security awareness.
In a hyperconnected digital landscape, viewing the internet as an attack vector is not merely important—it’s essential for safeguarding against a wide spectrum of cyber threats.
How can we help?:
Our User Awareness & Education equips your workforce with the knowledge and skills needed to identify and respond effectively to potential security risks. By educating your teams about common attack vectors such as phishing emails and social engineering tactics, we can help you empower every employee in your organisation to become vigilant gatekeepers against cyber threats.
Our Cyber Essentials Certification service is a comprehensive solution designed to assist organisations in achieving higher standard of cyber security and reducing the risk of breaches by 80%. Completing your Cyber Essentials Certification allows you to implement basic controls to reduce your external attack surface, such as:
Boundary Firewalls and Internet Gateways: Configure robust firewalls and gateways to protect your network perimeter from unauthorised access and malicious traffic.
Secure Configuration: Ensure that your systems are configured securely, following industry best practices to minimise vulnerabilities due to misconfigurations.
Access Control: Establish stringent access controls to limit user access to necessary systems and data, regularly reviewing and updating permissions.
A Microsoft 365 Security Gap Analysis is an essential step in fortifying your organisation’s cyber security defences. A M365 Security Gap Analysis is a methodical evaluation of your organisation’s security protocols and practices. Our aim is to pinpoint any shortcomings or weaknesses in your overall security posture and provide actionable steps for you to achieve your highest security potential. It not only reduces your external attack surface but also ensures compliance, enhances threat mitigation, and bolsters your overall security posture. It’s a proactive investment in the protection of your organisation’s security, data, and reputation in a modern day, threat-prone landscape.

Keep up with the ever-evolving world of Microsoft Security and the latest developments in cyber by signing up to Access Granted.
Your monthly cyber security round-up.