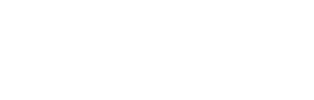
Microsoft Entra ID: Formerly known as Azure AD,
Microsoft Entra ID enhances identity and access management (IAM) capabilities, which are foundational to a zero-trust model. It provides features such as conditional access, which ensures that only devices and users that comply with your security policies can access your network, and multifactor authentication (MFA), which adds an additional layer of security by requiring multiple forms of verification.
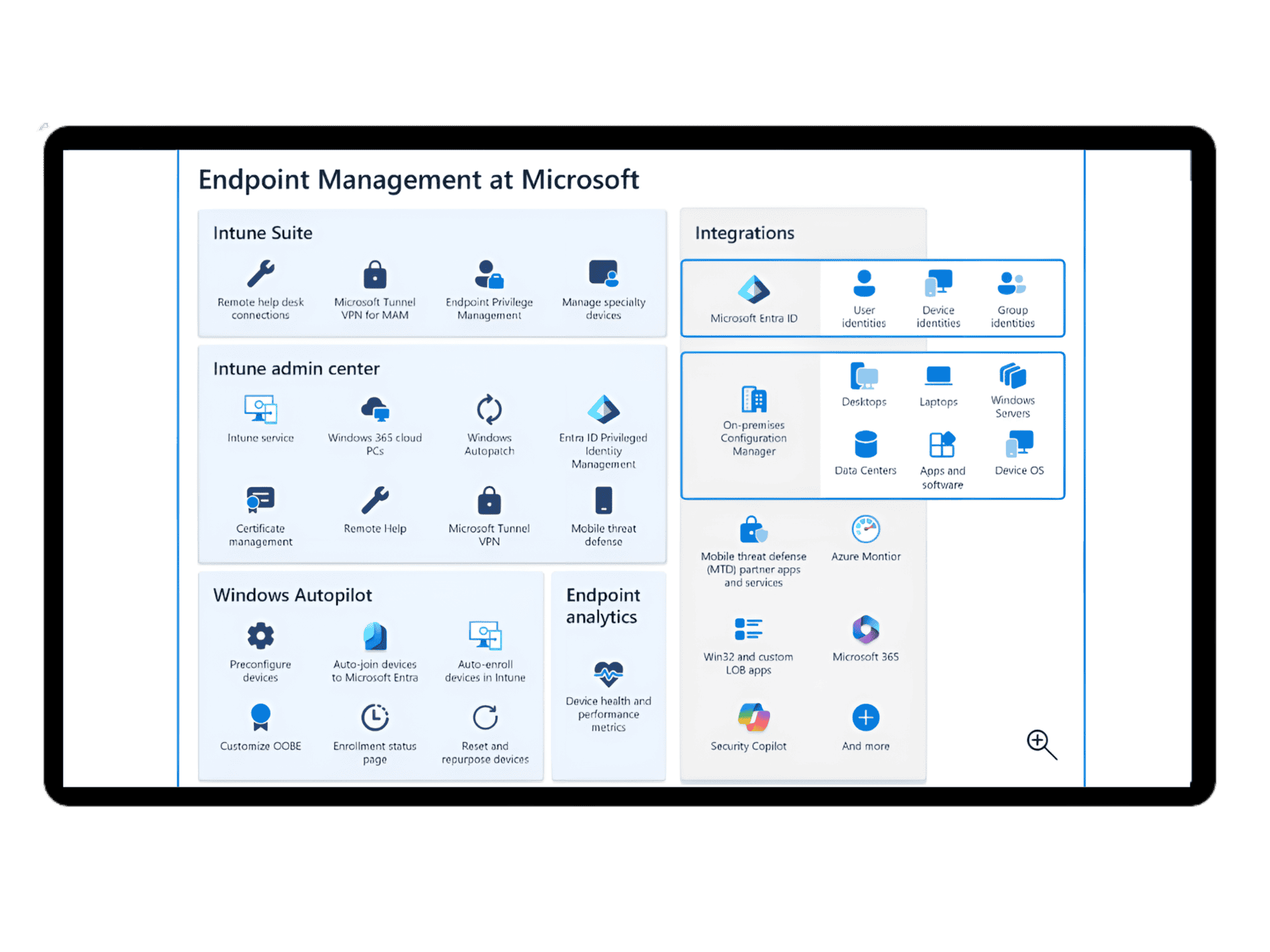
By leveraging these tools to enforce policy and monitor compliance, organisations drastically improve their overall systems and information security without impacting users’ ability to perform their duties.
Additionally, Microsoft Defender uses a behavioural threat analytics engine – a layered approach to security that can dynamically adapt to new threats based on what they do without needing dictionary updates to provide protection against zero-day threats in a constantly shifting security landscape.